We are Latin America’s leading business intelligence platform
We’ve been in the market for 27 years, generating information and data with on-the-ground experts so that global and local companies can make the best business decisions.
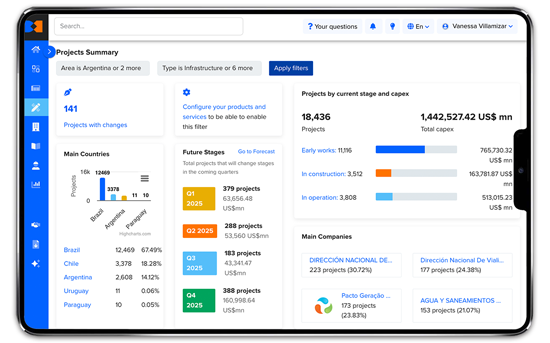
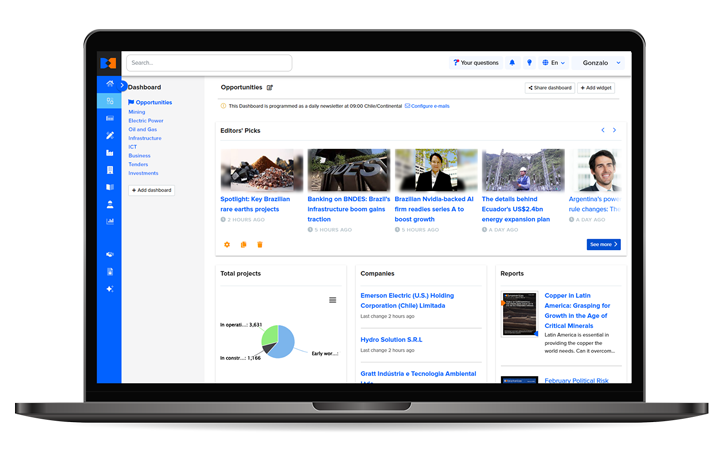
Reliable and complete data to make smart business decisions
We keep you up to date with the latest market trends to help you achieve your company’s goals.
Learn about the tools that will enable you to find key information
Project profiles
Learn the status of major projects in your industry of interest.
People profiles
Find contact details for thousands of high-level executives and project managers.
Company profiles
Analyze the outlook of your competitors or future customers with up-to-date information.
Pipeline
Manage your sales leads linked to the projects and companies highlighted on the BNamericas platform.
Reports
Get an in-depth understanding of your industry trends to anticipate what's coming.
Project profiles
Learn the status of major projects in your industry of interest.
People profiles
Find contact details for thousands of high-level executives and project managers.
Company profiles
Analyze the outlook of your competitors or future customers with up-to-date information.
Pipeline
Manage your sales leads linked to the projects and companies highlighted on the BNamericas platform.
Reports
Get an in-depth understanding of your industry trends to anticipate what's coming.
We cover Latin America’s main industries
Electric Power
Understand industry trends and access details on wind, solar, hydroelectric and thermoelectric projects, and more.
Explore Electric Power Explore Electric Power Explore Electric PowerFinancial Services
Get news about banks and insurance companies, as well as changes to tax, pension and investment regimes.
Explore Financial Services Explore Financial Services Explore Financial ServicesICT
Understand how digital transformation and technology is impacting different industries in the region.
Explore ICT Explore ICT Explore ICTInfrastructure
Get information about private and public sector investment plans and regulatory environment across the region.
Explore Infrastructure Explore Infrastructure Explore InfrastructureMining & Metals
Understand industry developments and get historical and current prices for copper, gold, silver and more
Explore Mining & Metals Explore Mining & Metals Explore Mining & MetalsOil & Gas
Learn about regulatory changes impacting investment and get historical and current prices for oil, gas and more.
Explore Oil & Gas Explore Oil & Gas Explore Oil & GasPetrochemicals
Stay on top of news about competitors, legislative changes and trend analysis.
Explore Petrochemicals Explore Petrochemicals Explore PetrochemicalsWater & Waste
Get news about regulations, competitors, political risks and trends in the wastewater and waste treatment industry.
Explore Water & Waste Explore Water & Waste Explore Water & WasteExclusive and up-to-date information daily
Our team of expert editors relies on artificial intelligence tools to collect data that will help you make better business decisions.
Clients
Learn what other local and global companies benefiting from our service have to say. Subscribing to BNamericas helps them grow their business!
"The mix of industry news, project info and reports produces interesting business opportunities in the main countries of the growing region & economy and to be up to date with the events."
James Lee Stancampiano - Head of Power Generation Chile & Argentina."BNamericas has become my source for information and news to support decisions and plans."
Jaime Soto - Director of Sales and Business Development Komatsu"At a corporate level, SMBC has come to depend on BNamericas as it is a valuable resource to which to turn for daily intelligence information and monitoring of projects in the region."
Carl Adams - Executive Officer and Deputy Head of the Americas at SMBC"We’re pleased to use BNamericas’ services and count on their valuable information to complement our environment monitoring and business intelligence."
Beatriz Elena López Valencia - Strategy and Risk Specialist at ISA"I’ve been using the BNamericas tool for a couple of years and have found it to be extremely useful and efficient in comprehensively aggregating the most relevant industry news under one roof."
Carlos Barrera - CEO Atlas Renewable Energy"We have been subscribers for the last three years. We use the projects database extensively and found it very useful. We also value the interactions with the BNamericas team in terms of their intimate knowledge of the markets in region."
Mark Wainwright - Managing Director - Natural Resources at Turner & Townsend